Preamble: Feeding Forward
In today's world, the essence of the internet, data encryption, and even the decline of consumer access to local food producers can all be traced back to a singular historical moment: World War II. It was during this pivotal time that the roots of cybernetics were planted, shaping our modern understanding of control, communication, and systems theory. Originating in wartime efforts to create more effective anti-aircraft systems and later expanded to human psychology and social systems, cybernetics introduced a philosophy of centralized control. This philosophy has, over the decades, trickled down into various facets of our lives, including the ways we interact online and how we access essential resources like food.
The centralization born from cybernetics hasn't just altered the technological landscape; it's been pivotal in reshaping our ideologies and even our nutritional habits. Like the intricacies of a spider's web, this centralized system has spun a complex narrative that's impacted consumer access to local food, creating a feedback loop of nutritional starvation and herding us into large-scale, centralized systems.
To break free, we need a fundamental pivot, a reorientation around a new axis—one that prioritizes decentralized control, individual freedoms, and community well-being. This isn't merely an about-face; it's a call for introspection and profound transformation that transcends the digital to impact every aspect of our lives.
It's here where the cybernetic concept of "feedforward" comes into play. Unlike a feedback loop that reacts to past events, feedforward anticipates and prepares for the future. In cattleman terms, it’s like sending a scout ahead to navigate the best path, offering the trail boss information to proactively guide the journey. By adopting a feedforward approach, we can foster decentralization and pave the way for local food producers to regain market access, thereby reclaiming our digital and nutritional sovereignty.
As we journey through "A Cowboy History of the Internet," helmed by Trail Boss Texas Slim and anchored in the Cypherpunk Movement's principles, remember that the challenges we face and the solutions we explore are not merely digital. They are, fundamentally, human. So saddle up and join us as we seek ways to regain control over our digital lives and, by extension, our ideological and nutritional well-being.
Cypherpunks write code. We know that someone has to write software to defend privacy, and we're going to write it.
— Eric Hughes
The Cypherpunk's Manifesto, 1993
Introduction
In these times, understanding the internet is as essential as knowing the unspoken rules of the cattle drive. I'm writing to you today as Ruffshot June, the Executive Director of Texas Slim's Cuts (The Ad Agency for The Great American Rancher) and your Executive Editor at Texas Slim’s Cuts Publishing. Alongside Trail Boss Texas Slim, we'll guide you through the complex terrains of code, digital rights, and evolving technologies. Our journey marries Texas Slim's insightful work "A Cowboy History of the Internet" with the privacy-focused principles of the Cypherpunk Movement. Together, they paint a vivid picture of how the internet has morphed over time, its impact on our lives, and the critical role it plays in the freedoms we value.
For those unfamiliar with the lore of The Great American Cattleman, Texas Slim gave me the name "Ruffshot" for a reason. In cattle drives, a Rough Shot is a trusted individual who rides miles ahead of the herd to scout for obstacles, threats, or any other impediments. After this reconnaissance, he returns to the trail boss—Texas Slim in our case—with a mapped-out plan of action. The trail boss then makes the final call on the course to take. This relationship is symbiotic, built on mutual respect; respect for the trail boss's wisdom and for the vision of the rough shot. This dynamic serves as a fitting prelude to our exploration of "A Cowboy History of the Internet."
Texas Slim, the CEO of the Beef Initiative and my co-pilot at Texas Slim’s Cuts, is a seasoned navigator of the digital frontier. He introduces us to the internet's early years, a time less shaped by Silicon Valley and more akin to an open prairie—a space of text-based conversations and open-source aspirations. Unfortunately, this landscape has now largely been fenced off by big tech companies.
We're not going to go to that fourth and that fifth and that sixth layer that they're trying to herd us into: Web 3. What we're going to do is we're going to pivot back down; we're going to get back to the source of the seed of where all this came from within technology."
-Texas Slim, “A Cowboy History of the Internet“
Complementing this is the Cypherpunks, who, armed with cryptography and a steadfast belief in privacy, champion the internet as a bastion of personal freedom and autonomy.
With these two perspectives in hand, we will dissect the underlying technologies of the web, like TCP/IP and DNS, while critically examining the societal implications of data centralization and monopolistic influence. Our ultimate goal? To sketch out a roadmap for reclaiming the internet as a space of freedom, nurtured by its decentralized origins.
A Brief Explanation of Technical Terms
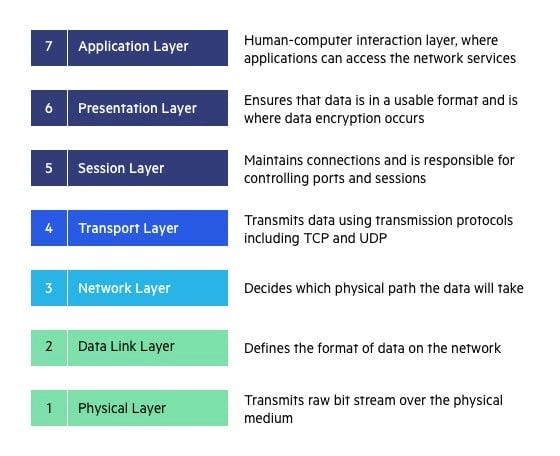
Layers of the Internet
Layer 1 - Physical Internet Wires: This is the foundational layer that consists of the physical infrastructure like cables and switches that make up the internet.
Layer 2 - TCP/IP and DNS: This layer contains the core protocols that enable the internet to function. TCP/IP (Transmission Control Protocol/Internet Protocol) is responsible for data transmission, while DNS (Domain Name System) translates human-readable domain names to IP addresses.
Layer 3 - Big Tech Giants: This layer is dominated by companies like Google, Facebook, and Twitter. They act as gatekeepers and have a significant influence on how we interact with the internet.
TCP/IP
Transmission Control Protocol/Internet Protocol: This is a set of rules that governs the way data packets are sent and received over the internet. It ensures that data reaches its destination accurately and efficiently.
DNS
Domain Name System: This system translates human-readable domain names (like www.beefinitiative.com) into numerical IP addresses that computers can understand.
Application Layers
These are software components built on top of Layer 3 that provide various services and functionalities. Examples include web browsers, email services, and social media platforms.
Censorship
This refers to the practice of suppressing or controlling content on the internet. In the context of Layer 3, big tech giants may employ censorship mechanisms to filter or block certain types of content.
Big Tech Giants
Companies like Google, Facebook, and Twitter that have a significant influence on how we access and interact with the internet. They are often considered the new gatekeepers of the online world.
Section 1: The Dawn of the Online Age and Evolution of Internet Protocols
Rewinding the clock to the early 1980s, we find the actual groundwork of the internet being laid. This wasn't merely a Silicon Valley phenomenon: the development of TCP/IP, which became the standard for ARPANET as of January 1, 1983, was a collective endeavor involving a variety of institutions across the country. Pioneers like Robert Kahn and Vint Cerf were instrumental in this effort, and it was about more than just young tech cowboys dreaming big—it was about collaborative ingenuity aimed at decentralization and freedom.
The same holds true for DNS, which was developed by Paul Mockapetris. DNS simplified the way we interact with the internet, making it accessible to everyday users. This was no small feat and shifted the internet from a specialist tool to a public utility.
Yet as we all know, the best-laid plans often go astray. Over time, we've seen increasing efforts by powerful tech companies to centralize the internet, which has led to a new dichotomy. The internet now has dual potential: it can either serve as a tool for individual freedom or as an apparatus for corporate-state control.
The key question we aim to address here is whether these two visions of the internet can coexist. We argue that by refocusing on the foundational protocols and principles that guided its early development, we can reclaim the essence of the internet as a space for individual freedom. It’s a mindset thang.
Section 2: Philosophical Foundations and the Rise of Big Tech
The foundations of the internet are not just circuit boards and code; they're also deeply rooted in philosophical ideals. Folks like Austrian economist Friedrich Hayek and his High-Tech Hayekian disciples have profoundly shaped these ideals. Their advocacy for decentralization and individual empowerment echoes the internet's original mission to serve as a tool for human freedom.
However, that philosophical core has come under siege, notably from big tech corporations like Google, Facebook, and Twitter. Their rise to prominence has shifted the landscape dramatically, steering the internet from its decentralized origins toward a more centralized model focused more on profit than privacy.
Texas Slim, never one to mince words, has been outspoken about this drift away from the internet's founding principles. He emphasizes the crucial need to understand the internet's underlying architecture. By reorienting ourselves toward cornerstone protocols like TCP/IP and DNS, Texas Slim contends that we can resist the centralizing pull of big tech and reclaim the web as a realm for personal freedom.
This sentiment is echoed by advocates of the Cypherpunk Movement, who view cryptography as a safeguard for privacy and a counterweight to corporate overreach. Their philosophy dovetails with Texas Slim's call for a return to the internet's decentralized roots, reinforcing the idea that the fight for internet freedom remains very much alive.
Section 3: The Birth of E-Commerce and Its Impact on the Beef Industry
The internet's ascent didn't merely alter the ways we connect and communicate—it also revolutionized business transactions. Take the American Information Exchange (AMEX), for instance, a trailblazer in the evolution of online markets. This new commercial frontier impacted a wide range of sectors, including ones as traditional as beef production.
As a Modern-Day Cattleman, Texas Slim offers a lens on this intersection that you won't find in a tech company boardroom. E-commerce, with its borderless marketplaces, presented both opportunities and pitfalls for the beef industry. While it expanded the customer base, it also further centralized commerce and financial systems, often pushing small ranchers to the margins in favor of massive corporations.
Not one to sit idly by, Texas Slim rolled out the Beef Initiative. This endeavor aims to harness the internet to benefit cattle producers in ways that break the mold. It proposes shifting away from the parts of the internet monopolized by big tech and returning to foundational layers and protocols. In doing so, the Beef Initiative offers ranchers a framework for protection, effective marketing, and data-driven decision-making, helping to decentralize the industry once more.
Though the Cypherpunk Movement is mainly focused on safeguarding digital liberties, they find common ground with Texas Slim's ethos. Both narratives advocate for using the internet as it was initially envisioned—a decentralized landscape that empowers individuals rather than accumulating power in the hands of a few.
Section 4: Pivoting Back to Layer 2: A Path to Internet Sovereignty
The internet isn't a singular monolith; it's a complex, multi-layered ecosystem. Texas Slim puts a spotlight on the importance of understanding these layers—especially what he calls 'layer 2' (layers 4-6 in the diagram below). This is the layer where the bedrock protocols like TCP/IP and DNS reside, the protocols that keep the internet's gears turning smoothly.
Over recent years, however, attention has swung towards the upper layers, zones increasingly monopolized by big tech giants such as Google, Facebook, and Twitter (Layer 7 in the model above). These platforms act as the new gatekeepers, often shaping our perceptions and understanding of the world. But as Texas Slim points out, these platforms are more than just gatekeepers; for those who know where to look, they can serve as springboards to deeper truths.
Right now we're stuck on that third layer really, and it's an interface surface level layer. When I say that, I'm talking about all the social media companies, all these big tech companies, these software companies that basically innovated extremely powerfully. But the more they innovated, the more they closed off and centralized what we call the internet. They created indexes; we have Google. Guess what, folks? Google isn't the Internet; it's just the index that they built.
-Texas Slim, “A Cowboy History of the Internet“
The real opportunity, according to Slim, lies in pivoting back to this foundational 'layer 2.' Doing so lets us sidestep the central authority of big tech and reconnect with a freer, more open internet. This isn't merely academic pontificating—it's a practical roadmap to digital self-determination. It involves leaning on tried-and-true technologies, like web servers and HTTP(s), blog CMS platforms, and ping APIs, technologies that have been serving us well since the 20th century, to regain control of our data and digital presence.
A Brief Explanation of Technical Terms
HTTP(s): Stands for HyperText Transfer Protocol (Secure). It's the set of rules for transferring web content—like text, images, and videos—between a web server and your browser. The 's' in HTTPS indicates an added layer of security.
Blog CMS Platforms: CMS stands for Content Management System. These are platforms like WordPress or Joomla that allow users to create, manage, and publish content on the web without needing to know how to code.
Ping APIs: API stands for Application Programming Interface. Pinging an API is a way to send a request to a web server for specific data or actions. For example, a weather app on your phone pings a weather API to retrieve the latest forecast.
These technologies aren't new; they have been around since the late 20th century. Yet, they remain foundational tools for maintaining an independent, user-controlled presence on the internet.
This approach dovetails neatly with the Cypherpunk Movement's focus on cryptography and basal protocols (or foundational rules for network communication) as instruments for personal freedom. It also intersects with the 'right to be forgotten,' a crucial web doctrine that allows people to take charge of their digital identities.
In advocating for this reorientation toward foundational layers, Texas Slim and the Cypherpunks are pushing back against the narrative of centralization and control that has come to characterize today's internet. In its place, they offer a vision of a digital landscape that is empowering, free, and sovereign.
Section 5: The Forgotten Technologies of Freedom
As we navigate the complexities of the modern internet, it's easy to forget that many of the technologies that offer the most freedom have been around for decades. Web servers, HTTP(s), blog CMS, and ping APIs have existed since 1999 and offer a level of data control and freedom that is often overlooked in discussions about internet sovereignty.
These technologies allow for full control over one's data, from creation to deletion. They offer features like discoverability and the "right to be forgotten," which are now being clumsily implemented at the client level in newer systems like Nostr. Texas Slim and the Cypherpunk Movement both argue that these existing technologies can serve as robust alternatives to the centralized platforms that dominate the internet today.
For instance, self-hosted weblogs run by open-source CMS give users maximum data control. You can decide not to appear on any trend lists, control who sees your data, and even delete it entirely. This level of control is unparalleled and aligns closely with the principles of both Texas Slim and the Cypherpunks.
The question then arises: Why do we need new, centralized systems when we already have technologies that offer greater freedom and control? Texas Slim suggests that by focusing on these forgotten technologies and pivoting back to foundational internet layers, we can reclaim the internet as a space for individual freedom and sovereignty.
This perspective is not just a nostalgic look back but a practical guide for the future. It serves as a reminder that the tools for a free and open internet already exist; we just need to use them effectively.
Section 6: Societal Impact: Attention, Behavior, and Algorithms
The internet's influence extends far beyond the realm of commerce and data control; it has a profound impact on human behavior and attention. Algorithms, particularly those employed by social media platforms, have been designed to capture and hold our attention. These algorithms prioritize short-form, quick-cutting videos and sensational content, often at the expense of depth and nuance.
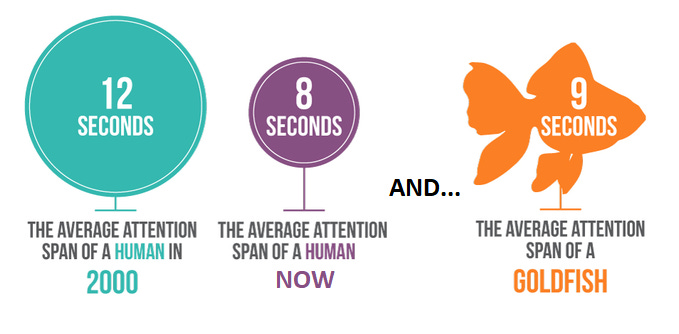
Texas Slim points out that this shift towards algorithmically curated content has implications for our collective attention span. Studies have shown that the average human attention span has decreased from 12 seconds in the year 2000 to 8 seconds today, which is even shorter than the attention span of a goldfish. This decline is not just a quirky statistic but a societal concern, affecting everything from our ability to engage in deep work to our mental well-being.
The Cypherpunk Movement, although primarily focused on digital privacy, also acknowledges the societal impact of these algorithms. They advocate for a more conscious use of technology, one that respects individual autonomy and encourages meaningful engagement rather than mindless scrolling.
The question of algorithmic influence also ties back to the issue of centralization. When a few big tech companies control the algorithms that dictate our online behavior, the internet becomes less of a tool for individual empowerment and more of a mechanism for mass control. Both Texas Slim and the Cypherpunks see this as a deviation from the internet's original promise of freedom and sovereignty.
By understanding the impact of algorithms and making a conscious effort to pivot back to foundational internet layers, we can reclaim control over our digital lives. This is not just about data privacy but also about mental space, attention, and ultimately, human dignity.
Section 7: Cryptography as the Key to Personal Liberation and Privacy
In today's digital landscape, where data has become as valuable as any traditional currency, the need to protect it is paramount. Cryptography, the practice of securing communications, has risen to prominence as an essential means of safeguarding personal freedom and privacy online. Leading this charge is the Cypherpunk Movement, which has tirelessly campaigned for the adoption of cryptographic techniques as a bulwark against intrusive government surveillance and corporate data harvesting.
While Texas Slim's main expertise lies in the cattle industry and the structural anatomy of the internet, he too recognizes the crucial role of cryptography. He views it as a synergistic tool that can mesh well with foundational internet protocols like TCP/IP and DNS. Together, they can lay the groundwork for a decentralized and more secure digital world.
The watershed moment for cryptography came in the 1990s when public sentiment in the United States was largely antagonistic towards encryption technologies. Governments saw encryption as a dual-edged sword, a legacy from its impactful role in World War II. Despite this resistance, the Cypherpunks pushed back, ultimately securing the right to use encryption, which is now ubiquitous across various platforms and protocols.
Fast forward to today, and the battle lines are being drawn once more as several western democracies are attempting to curb the use of end-to-end encryption. Both the Cypherpunks and Texas Slim view this as a retrograde move, a departure from the founding principles that envisioned the internet as a platform for personal freedom and sovereignty.
By understanding and adopting cryptography's capabilities, we are making strides towards reclaiming the internet as a sanctuary for individual liberties. It serves as an enduring reminder that the struggle for an open and free internet continues, and the instruments we need to win this battle are already within our reach.
Section 8: Warnings for the Future
As we cast our gaze towards what lies ahead for the internet, it's vital to listen to the sage advice of those who have been scrutinizing its development for years. David Burnham, a journalist with The New York Times, sounded early alarms about the perils of automated surveillance—a concern that has magnified in an era dominated by big tech giants and expansive government watch programs.
Texas Slim and the Cypherpunk Movement resonate with these early warnings, urgently advocating for a pivot back to the internet's foundational philosophy of decentralization and personal sovereignty. They contend that the internet's current path, characterized by escalating centralization and regulatory control, stands in stark contrast to the core principles upon which it was conceived.
The Beef Initiative spearheaded by Texas Slim, as well as the Cypherpunks' relentless push for the widespread use of cryptography, serve as pragmatic measures aimed at reclaiming this lost decentralization. By centering their efforts on the internet's foundational layers and encrypted communications, these actions chart a course towards an online landscape that is more liberated, autonomous, and aligned with its initial vision.
This broader debate also intersects with discussions about the evolving roles of large institutional bureaucracies and the notion of representative democracy in this digital epoch. As we wade through the intricate maze of today's internet, a pivotal question looms: Can we successfully course-correct towards a more decentralized framework, or are we irreversibly headed towards a future under centralized dominion?
According to both Texas Slim and the Cypherpunks, the solution resides in our collective efforts. By delving into the internet's structural nuances, rekindling interest in older yet potent technologies, and championing the cause of digital privacy, we have the chance to reshape the internet as an instrument for both personal liberty and broader social advancement.
Conclusion
The internet has metamorphosed from its humble beginnings as a text-centric, open-source platform to a multimedia colossus largely under the thumb of big tech corporations. This essay has ventured through this nuanced trajectory, guided by the wisdom in Texas Slim's "A Cowboy History of the Internet" and the guiding principles of the Cypherpunk Movement.
We explored the philosophical bedrock that has given form to the internet, assessed the ascendancy of e-commerce and its ramifications on sectors like beef production, and considered the societal impact of algorithm-powered platforms. We also scrutinized the vital role of cryptography in safeguarding digital privacy and underscored the imperative of reclaiming the internet's foundational ethos of decentralization and personal freedom.
Texas Slim and the Cypherpunks not only critique the status quo but also furnish actionable roadmaps. Whether it's a strategic shift back to the internet's elemental layers, reviving overlooked technologies, or advancing secure methods of communication, the blueprint for a freer and more open internet is palpable and within reach.
As we find ourselves at this pivotal digital juncture, the decisions we make will indelibly shape the future digital landscape. We already have at our disposal the tools needed for a secure, decentralized, and individual-focused internet; what remains is our collective will to deploy them adeptly. In doing so, we can restore the internet as a domain for personal liberty, societal betterment, and, in the words of Texas Slim, a fulcrum for discerning the truth.
Take a Stand Against Big Tech
The quest for an open, decentralized internet isn't merely an idealistic dream—it's an urgent call to action that demands calculated efforts across multiple spheres. Below is a comprehensive roadmap for addressing this pressing issue:
Technical Strategies
Public Education: Raise awareness about the indispensable role of foundational protocols like TCP/IP and DNS in sustaining a decentralized internet. Internet Society, TeachPrivacy
Champion Open Standards: Advocate for open, community-supported standards that elude the grasp of singular corporate entities. W3C, OpenStand
Support Decentralized Technologies: Promote transformative technologies like Bitcoin and peer-to-peer systems that further decentralization. Bitcoin.org, Peer-to-Peer Foundation
Bolster Security: Reinforce essential protocols to defend against susceptibilities and cyberattacks. Cybersecurity & Infrastructure Security Agency, OWASP
Preserve Net Neutrality: Advocate for net neutrality to thwart ISPs from compromising the very soul of a decentralized internet via preferential data routing. Save the Internet, Fight for the Future
Sociopolitical Strategies
Legal Reforms: Lobby for legislative measures that curb monopolistic behaviors and encourage a decentralized web environment. Electronic Frontier Foundation, Public Knowledge
Educate Consumers: Raise public awareness about the benefits of decentralization, including increased privacy and control over personal information. Privacy Rights Clearinghouse, Consumer Reports Digital Lab
Grassroots Connectivity: Invest in or support community-driven internet initiatives that emphasize foundational protocols. Community Networks, Freifunk
Strategic Partnerships: Form collaborations with academics, intellectuals, organizations, and policymakers who share the mission. Open Technology Institute, Data & Society
Demand Transparency: Urge corporations to be forthright about their data management practices and the protocols they employ. Transparency Toolkit, OpenCorporates
By executing these diversified strategies—covering technical, sociopolitical, and economic angles—we can counteract the centralizing impulses of big tech and reaffirm the internet as a haven for individual liberty and self-determination.
Special thanks to: mslm dvlpmnt for technical insights
Calls to Action
1. Support Our Cause
Rally Behind The Beef Initiative
You have the power to make a difference. Here’s how you can support our mission.
Upgrade Your Dinner: Get a Beef Box
Invest in the Cause: Make a Donation
Stay Informed: Subscribe for Updates
2. Affiliate Links
Claire & Fritz Tallow Shop
Clara and Fritz invite you to be part of a generational movement. Let's regenerate - our skin, our relationships, our collaborations. Dive into the world of skincare with products crafted from beef tallow. It's time to understand regenerative collaboration. Begin your journey with Clara and Fritz. Let's regenerate together. Our newsletter subscribers get 10% off!
3. Become an Affiliate
Unlock Earnings with Our Affiliate Program
Become part of our movement and earn commissions on the sales you refer. Click below for details.
Learn & Earn: Affiliate Program Information
4. The Beef Initiative Association Council
Join the Beef Initiative Association Council
Our Commitment
At TBIAC, our mission is to deliver unparalleled data-driven insights to micro-processing facilities, both in Texas and nationwide. Guided by unwavering integrity, we rely on verifiable results as we collaborate to nourish local communities sustainably. Your partnership is our strength—let's build a better future from the inside out
5. Get Involved
Play Your Part—Volunteer Today!
Time and expertise are gifts. Offer yours to a cause that matters.
Open Position: Experienced in graphic design or storytelling? We'd love to hear from you.
Connect: Reach out to us at info@beefinitiative.com to get started.